Median reduction in paid log volume for early adopters in the first 90 days.
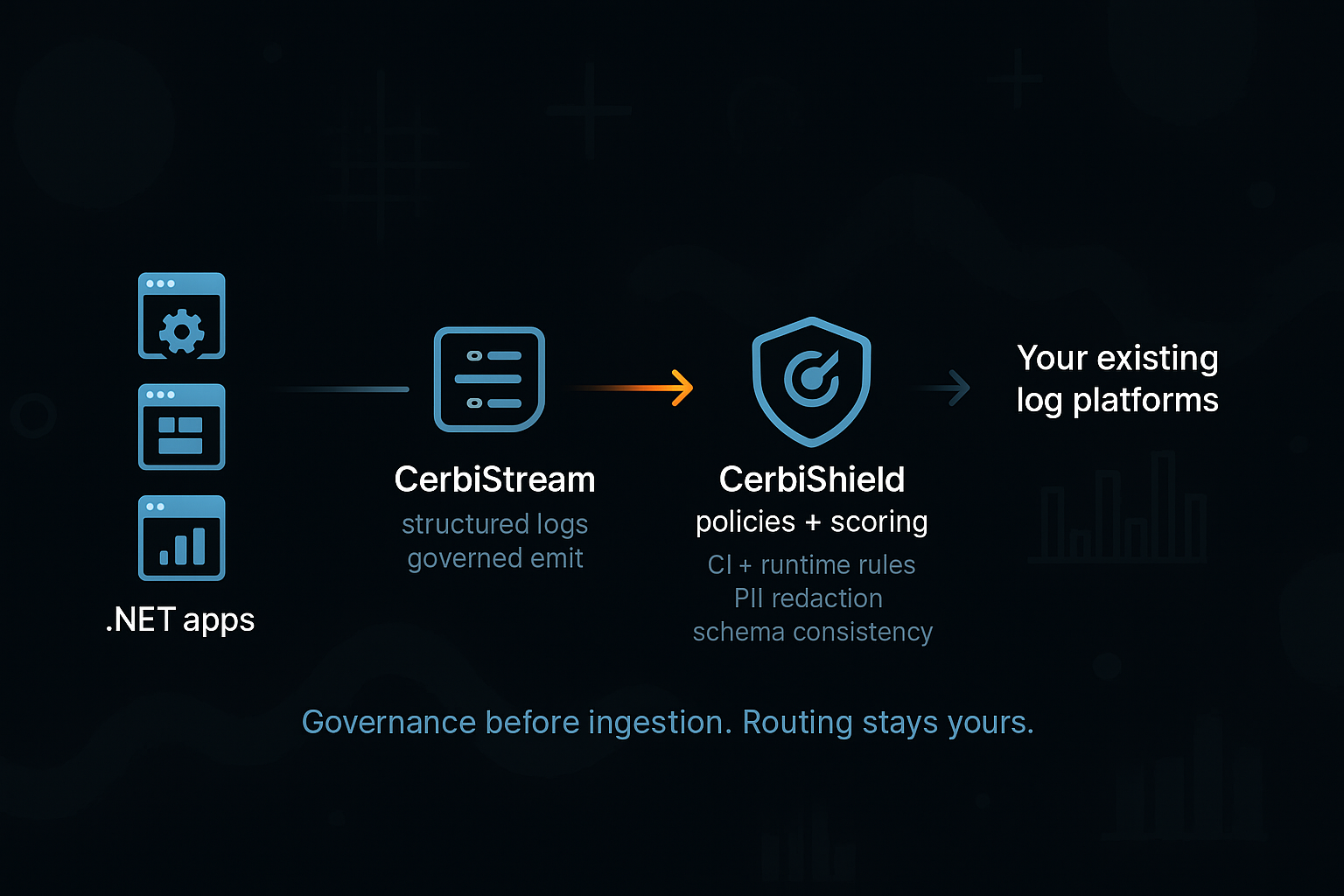
Govern logs before they reach your log platforms.
CI + runtime guardrails for structured logging and automatic redaction—without swapping out your log destinations or observability tools.
- Enforce .NET log schemas at the source (MEL / Serilog / NLog).
- Strip PII/PHI before Azure Monitor / Datadog / Splunk.
- Score governance posture over time for audits & AI.
Cerbi is a tenant-hosted logging governance control plane. CerbiStream, the Governance Analyzer, and runtime enforcement stay free on NuGet; paid value lives in CerbiShield dashboards, lifecycle, scoring visibility, deployment, reporting, and RBAC.
Compliance checks passed on first audit when teams enforced Cerbi governance profiles.
Time-to-resolution improvement after instrumenting runbooks with governed, searchable logs.
Figures are illustrative pilot outcomes from governed schemas, redaction posture, and audited evidence; your pipeline and controls will change results.
Outcomes at a glance
Cost, compliance, and quality wins come from governing before ingestion—while your routing to log destinations stays yours.
Cut paid log volume
Drop noisy fields and junk events at the source to trim ~40% of paid ingestion without changing collectors.
Prove redaction posture
Versioned profiles, deployment history, and runtime enforcement create an auditable trail for regulated workloads.
Stabilize dashboards
Schema guardrails and governance scores keep dashboards, alerts, and ML features consistent across releases.
Three steps to governed logging without rerouting traffic
CerbiStream + CerbiShield provide tenant-hosted governance. You keep routing logs to any vendors or storage you choose.
Define governance profiles
Author required/forbidden/sensitive fields and redaction rules as JSON. Profiles live in your repos for review and promotion.
Enforce in CI + runtime
NuGet analyzers block schema drift in CI; runtime validators tag/redact violations without taking over your collectors or log destinations.
Score and prove posture
CerbiShield tracks deployment history, RBAC, and governance scores so you can show improvements over time—while your log routing stays unchanged.
See the product before you try it
Dashboard-first visuals that show how Cerbi governs before ingestion while you keep routing to your log destinations.
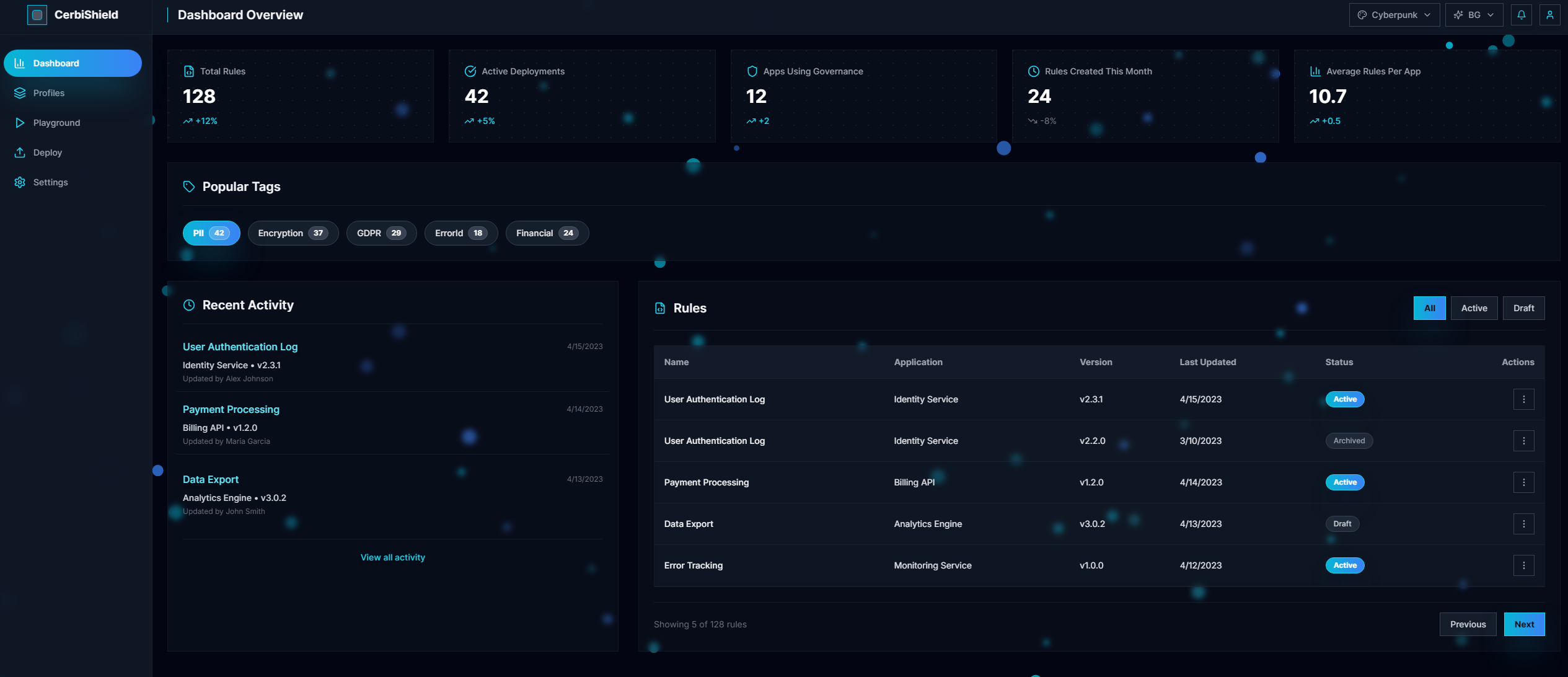
Scores, violations, and governed apps in one tenant-hosted view.
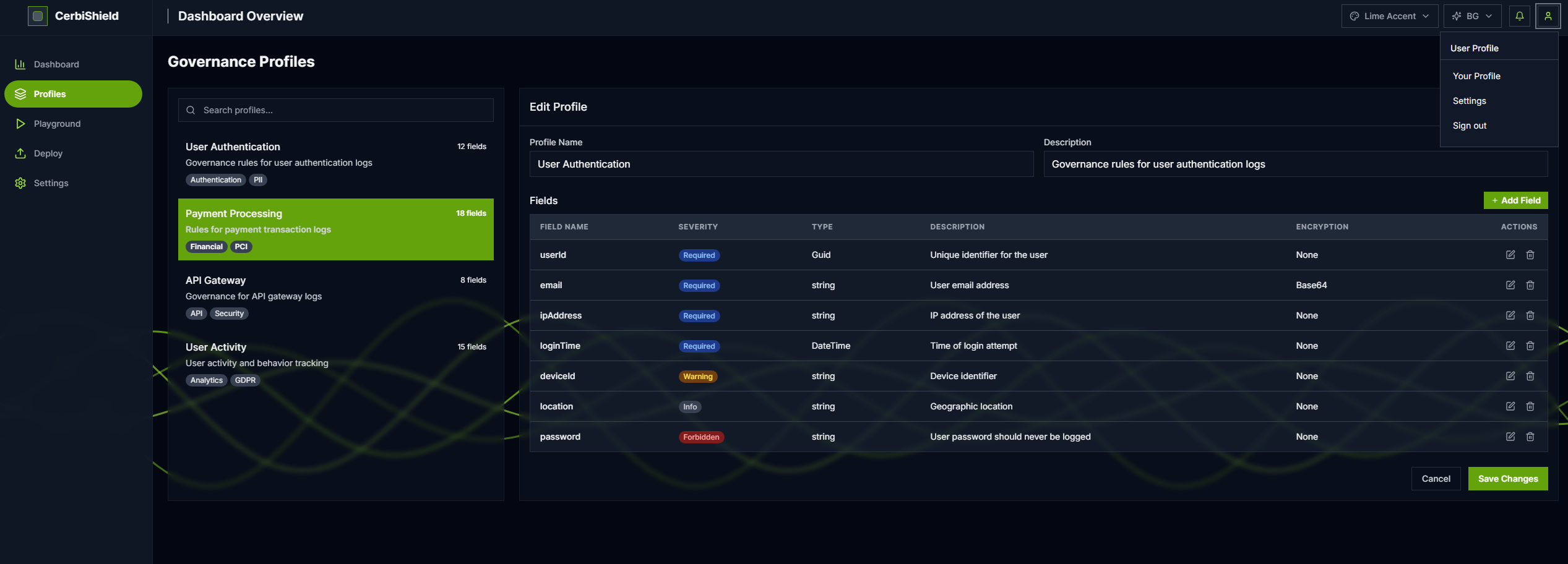
Define required, forbidden, and sensitive fields with versioned governance.
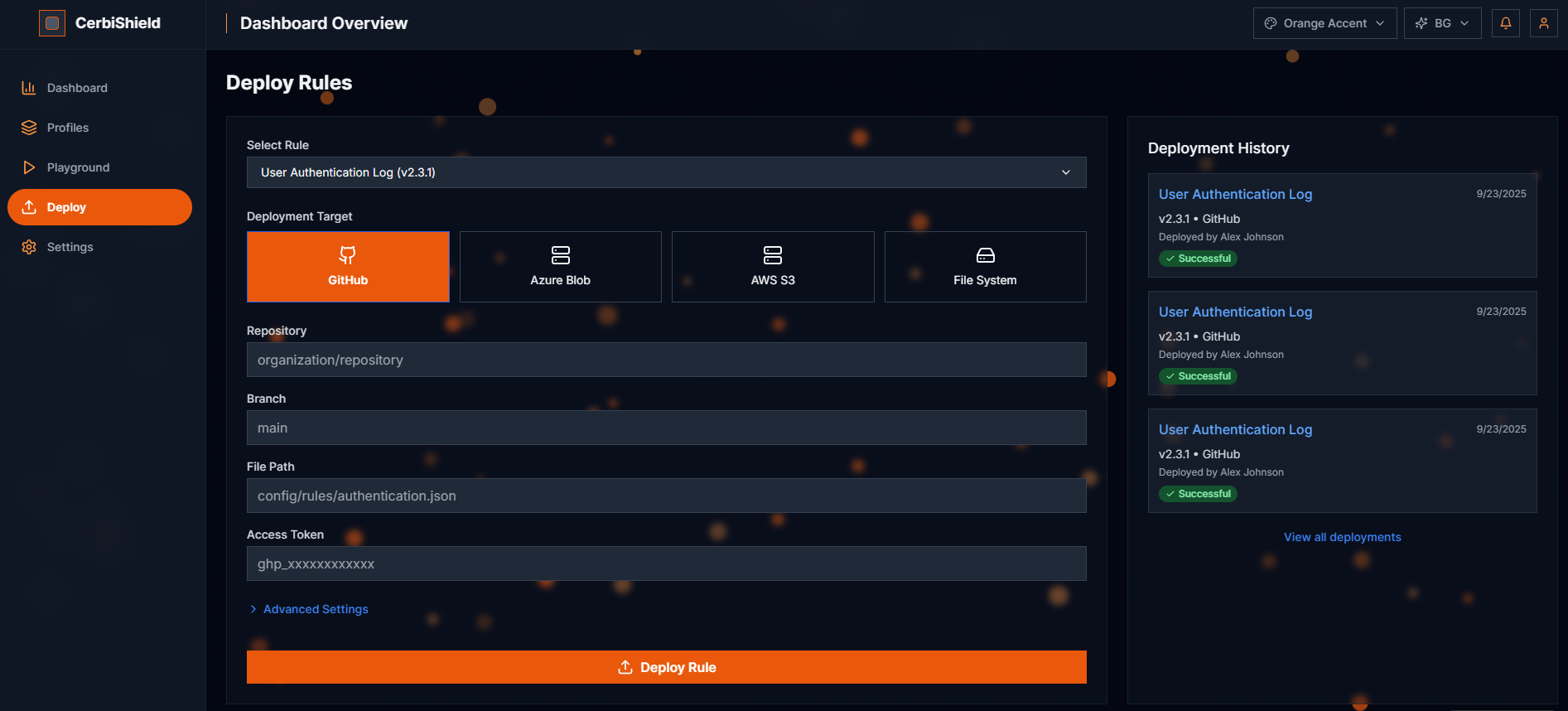
Trace when governance changes moved to each governed application.
Use Cases (for teams & execs)
Short, concrete wins you can expect. Each can start small and expand safely across the org.
Outcome examples are illustrative pilots grounded in governance controls, redaction posture, schema stability, and audit evidence; expect variance by stack.
1. Cut Log Spend
Normalize fields, roll up noise, and de-duplicate before indexing.
- Govern logs at the source with versioned schemas and redaction before anything leaves the service
- Score governance outcomes release-over-release so you can prove controls are working
2. Prove Compliance
Versioned PII policy + redaction metadata you can hand to Risk/Legal.
- Keep your logger and pipeline while policy rides along to any log destinations you choose
- RBAC & audit history in CerbiShield
3. Stabilize Dashboards
Stop breaking charts every sprint due to field drift.
- Stable names & types
- Durable alerts across releases
4. Accelerate Incidents
Consistent app/env/tenant/trace IDs → faster triage and MTTR.
- Joinable logs across services
- Violation context included
5. Ship ML-Ready Telemetry
Clean, governed features for LLMs & models—without PII surprises.
- Tags, categories, enums
- Consistent shapes for training
6. Adopt Gradually
Start with one domain, run in relax-mode, then tighten.
- Keep your loggers/log destinations
- No vendor lock-in
Pricing that tracks governed applications
Pricing is based on governed applications — not environments or traffic. One app across dev/test/uat/stage/prod counts as one license.
CerbiStream + CerbiShield provide tenant-hosted structured logging governance. Cerbi does not route logs to vendors; you keep your collectors and destinations.
What counts as an app? A single governed application or service, even if it spans dev/test/uat/stage/prod. When microservices are governed separately, they count individually.
Pricing is by governed applications — not environments or traffic. One app across dev/test/uat/stage/prod counts as one license.
Validate CerbiStream locally with baseline governance and redaction patterns.
- MIT-licensed analyzers + runtime governance
- Governance profiles stored in your repo
- Local audit history for change awareness
- Works with your existing logging and routing
Add lightweight RBAC and CI enforcement for small teams.
- Analyzer enforcement to block schema drift
- Email or SSO access with audit logs
- Deployment targets for test + prod parity
- JSON import/export for governance-as-code
Most popular for platform teams standardizing schemas with traceable history.
- CerbiShield dashboard + governance lifecycle
- RBAC depth with SSO/SCIM and approval flows
- Versioned governance profiles with deployment history
- Scoring visibility and reporting rollups
For large estates needing governed reporting and broader app coverage.
- Hierarchical RBAC and SCIM provisioning
- Governed reporting exports for internal reviews
- Regional deployment targets with rollback metadata
- Priority support and private offer options
Pricing is provisional for Marketplace previews; final terms, limits, and SLAs will be confirmed in order forms or private offers. Cerbi governs schemas and redacts/tag payloads but leaves log routing entirely under your control.
Frequently Asked Questions
Get quick answers to common questions about CerbiSuite. Still have questions? Contact us below.
Is this just another logger?
No. CerbiStream is a governance-first logger. While traditional loggers focus on capturing data, CerbiStream adds built-in governance, compliance validation, PII redaction, and ML-ready structured output. Think of it as a logger + compliance engine + data quality platform in one.
How hard is migration from Serilog or NLog?
CerbiStream uses familiar .NET logging abstractions and can run alongside Serilog, NLog, or MEL during rollout. You can enable Cerbi for a subset of services first, validate governance profiles, and then expand as you gain confidence. Many teams can prototype integration in a day or less, but full cut-over timing depends on your codebase and the governance rules you choose to enforce.
Where is my data stored? Do you have access to it?
CerbiStream writes logs to destinations you configure (files, databases, queues, SIEMs) inside your environment. We don’t operate a centralized log-ingestion SaaS, and we don’t have access to your application log payloads. Optional analytics features can work on derived governance metadata if you explicitly enable them, but raw logs remain under your control.
What about performance? Will this slow down my application?
CerbiStream is designed to stay off the hot path. Logging uses async Channel-based buffering so application threads aren’t blocked, and governance validation runs in the background. In our BenchmarkDotNet tests on typical .NET workloads, CerbiStream’s overhead was comparable to established .NET loggers. Exact numbers depend on your payloads, sinks, and governance rules.
What .NET versions does CerbiStream support?
CerbiStream targets .NET 8 and .NET 9 on NuGet, with computed compatibility forward to .NET 10+. Older services on .NET 6 or .NET 7, as well as legacy .NET Framework apps, can integrate through the Microsoft.Extensions.Logging abstractions or adapter patterns, but first-class support and testing focus on the current runtimes.
Is CerbiSuite open source? What's the licensing model?
CerbiStream core and the shared governance libraries (for example, Cerbi.Governance.Core and Cerbi.Governance.Runtime) are open source under the MIT license. CerbiShield (the governance dashboard, APIs, reporting, and scoring) is licensed commercially per governed application—not per environment—and includes support and SLAs. Check each repo or NuGet page for the exact license; runtime pieces are permissive, governance/dashboard/scoring are paid.
What makes CerbiSuite different from Datadog or ELK?
Datadog and ELK are observability platforms that consume logs. CerbiSuite focuses on log creation and governance at the source. Use CerbiStream to create high-quality, compliant logs, then send them to Datadog, ELK, or any other platform. We complement observability tools; we don't replace them.
Can I try it before committing? Is there a demo environment?
Absolutely! Use our 60-second Quick Start to install CerbiStream via NuGet and try it locally. For enterprise features, request a demo and we'll set up a sandbox environment with your data. No commitment required.
Cerbi is the governance layer for your existing logging stack
Enforce policies, validate payloads, and score redaction posture while your agents, collectors, and log destinations stay the same.
Why Redaction Alone Isn’t Enough
Cerbi complements Serilog, NLog, and Microsoft.Extensions.Logging by governing payloads before they hit your log destinations. Instead of relying on ad-hoc masking, Cerbi combines policy, analyzers, runtime guards, versioning, and scoring so redaction is one layer in a governed pipeline you keep routing.
Required/Disallowed/Sensitive policy
Define Required, Disallowed, and Sensitive field rules for every log shape so schemas are intentional and sensitive data is controlled by policy—not best-effort filters.
Build-time analyzers
Roslyn analyzers flag violations in CI before code ships, blocking schema drift and risky fields while keeping your existing logger configuration.
Runtime validation & redaction
Runtime validators enforce the same rules in production, redacting or tagging violations so payloads stay compliant without changing your transport.
Policy versioning + deployment history
Versioned policies with deployment traceability show who changed what and where it’s enforced, keeping governance decisions auditable release over release.
Scoring visibility
Scoring surfaces schema consistency, redaction posture, and coverage trends so teams can prove improvements and spot regressions quickly.
Who it’s for
Platform / SRE
Schema chaos blows up dashboards and on-call. Cerbi standardizes payloads at the source and flags drift before it ships—result: stable signals and calmer incidents.
Security / Compliance
Sensitive-data risk and missing audit evidence stall reviews. Cerbi enforces and versions policies in CI/runtime and records deployment history—result: traceable redaction posture you can hand to auditors.
Engineering Leads
Cross-team inconsistency slows releases. Cerbi keeps schemas versioned outside code, scores adherence, and blocks regressions in CI—result: consistent logs and faster approvals.

Built by a principal architect, not a marketing team
I’m Tom, a principal architect who’s spent years untangling .NET logging in regulated environments — healthcare, payments, and cloud platforms that actually get audited. Cerbi is the logging and governance layer I kept sketching on whiteboards and never got from vendors, so I built it.
CerbiStream runs in your .NET services. CerbiShield runs in your tenant. You keep your log destinations. Cerbi gives you governed, PII-safe, audit-ready telemetry without dropping another black-box SaaS in the middle.
Cerbi — Brief Overview
CerbiStream is a governance-first logging layer for .NET that validates, redacts, and tags every log event before it hits your log platforms. Instead of shipping “whatever the app logs” into expensive platforms, Cerbi enforces JSON profiles so only clean, compliant, ML-ready data flows downstream. CerbiShield is the tenant-hosted governance brain and scorecard layer that defines, versions, and deploys those profiles with RBAC and audit history—customers own the infrastructure and data plane while policy stays outside code. The Scoring API is the governance scoring engine that tracks posture over time. Together, they turn logging from an ungoverned cost center into an auditable, measurable part of your architecture without ever routing your traffic.
| Product | Type | Where it runs | License |
|---|---|---|---|
| CerbiStream | .NET logging library | In your apps/services | OSS (MIT) |
| Cerbi.Governance.Runtime | Engine | In your apps/services | OSS (MIT) |
| CerbiShield | Governance brain + dashboards | In your Azure tenant | Commercial |
| Scoring API | Governance scoring service | In your Azure tenant | Commercial |
Built for Compliance from Day One
Cerbi was designed for regulated workloads. Governance profiles let you define required, forbidden, and disallowed fields, plus redaction rules, so PII and PHI don’t leak into your log pipeline by accident. CerbiShield lets you version and deploy these profiles per app and environment, so auditors can see exactly what is enforced and where. We don’t promise “automatic compliance”—instead, we give you the guardrails and evidence you need to pass real audits.
Encryption at Rest & In Transit
AES-256 file encryption is available for fallback logs, and Cerbi fits cleanly into TLS-secured infrastructure. Exact cipher suites and TLS versions are controlled by your hosting platform and configuration. Cerbi does not weaken your existing security posture.
Automatic PII Redaction
Rule-based redaction identifies and masks sensitive fields before they are written to your log destinations. Governance profiles keep PII and PHI out of your log payloads by design. Optional analytics and future ML components can build on the same metadata, but core redaction is explicit and policy-driven.
Compliance Ready
Built-in audit trails and governance metadata are designed to help you address common SOC 2 Type II, HIPAA, GDPR, and ISO 27001 logging controls. Cerbi itself is not a substitute for legal review or formal certification, but it gives your security and compliance teams the evidence they expect from a modern logging layer.
Real-Time Violation Alerts
Catch governance violations quickly. Cerbi tags events with structured violations so your pipelines (OTel, Fluent Bit, Vector, custom collectors) can forward alerts into your existing stack (Splunk, Datadog, ELK, Grafana, etc.) before issues become incidents or audit findings.
Your Infrastructure, Your Control
By default, Cerbi runs entirely in your tenant so logs stay in your environment. Optional analytics services can consume derived metadata if you choose to enable them, but Cerbi does not ship your raw logs to shared SaaS by default.
Immutable Audit Logs
Append-only audit trails are designed to be stored in immutable or WORM-capable storage, making access and changes tamper-evident during investigations and audits.
AI-ready, not AI-locked-in
Cerbi doesn’t try to be your AI platform. It focuses on producing clean, structured, governance-tagged logs that any AI stack can consume. Whether you’re using Databricks, OpenSearch, self-hosted RAG, or vendor LLMs, Cerbi adds consistent fields like GovernanceViolations, GovernanceProfileUsed, and GovernanceRelaxed so downstream analysis and scoring stay predictable. You decide which models to run and where; Cerbi simply makes the data safe and usable.
Why CerbiStream Exists
As organizations scale across internal squads, contractors, and third-party libraries, logging becomes a patchwork—hard to trust, hard to use, and risky. Cerbi turns logs into governed, reliable data products.
| Approach | Pros | Cons | Best when… |
|---|---|---|---|
| "Just log more" | Fast to start | Inconsistent fields, PII risk, higher cost | Tiny apps, prototypes |
| Downstream normalization | No app changes | Late fixes, fragile | Short-term stopgap |
| Cerbi governance | Stable schema, redaction, versioned policy | Define profiles; add analyzers/validators | Multi-team apps, compliance |
The Cerbi Ecosystem
A cohesive suite where each component addresses a critical aspect of enterprise logging.
| Component | Status | Purpose |
|---|
Governance Scoring Flow
From runtime validation to dashboard visualization—governance signals flow to the Scoring API while your log routers keep sending payloads to the destinations you already trust.
Runtime Validators Compute ScoreImpact
Runtime validators and governance plug-ins grade each log against profile rules, compute the ScoreImpact, and tag the event before your router ships it.
- Severity-weighted scoring
- Plugin contributions
- Relax-mode support
Async, PII-Safe Scoring Payloads
Minimal scoring payloads (no PII) ship asynchronously to the Scoring API for ingest/normalize/compute ScoreImpact—non-blocking, batched, and separate from your payload routing.
- Non-blocking
- Batched
- Resilient retry
Persist to Store
Scoring API ingests the score metadata asynchronously and persists it to CerbiShield via Store APIs with RBAC and timestamps.
- EF migrations
- RBAC-aware storage
- UTC timestamps
Reporting Rollups
CerbiShield Reporting APIs roll up scores by service, environment, team, and time window.
- Flexible grouping
- Trend analysis
- Multi-dimensional rollups
Visualize Compliance
CerbiShield displays trends, violations, and scorecards with drill-downs.
- Realtime metrics
- Violation drill-down
- Team scorecards
Closed-Loop Governance & Scoring
A clear four-step loop that keeps schema consistency, redaction posture, and governance enforcement measurable—without changing how you route logs.
- Define policies (CerbiShield): author and version required fields, redaction rules, and relax modes as portable governance standards.
- Enforce at source (CerbiStream + analyzers + runtime validators): build-time analyzers and runtime validators block schema drift and PII leaks before data leaves the service.
- Score outcomes (Scoring API): the scoring engine normalizes governance signals and grades every event so schema quality, redaction posture, and coverage remain comparable across teams.
- Improve standards over time: scorecards feed back into CerbiShield so teams can tighten or relax policies confidently while services keep running.
The Scoring API is the governance signal normalization + scoring engine. The legacy “CerbIQ-as-router/normalization/fan-out” story is fully retired—CerbIQ is deprecated. Cerbi never brokers, forwards, or replaces your transport to Splunk, Datadog, ELK, OpenSearch, or any other sink.
Cerbi is not a log transport layer and does not require pipeline changes. Customers keep their existing routing (Kafka, Event Hubs, Vector, Fluent Bit, HTTP collectors, or anything else) while Cerbi layers governance, validation, and scoring metadata on top—your pipelines continue delivering payloads to vendors unchanged.
Why this matters for Platform & SRE
Platform and SRE teams get provable guardrails without re-platforming: consistent schemas, reduced incident blast radius from bad payloads, faster RCA from scored violations, and clearer ownership around who is enforcing what.
The Challenge → Our Solution
Clear problems, concrete solutions—for executives, security teams, and developers.
The Problem
Observability cost anxiety driven by noisy, unstructured logs and accidental ingestion.
Our Solution
Reduce noise before ingestion with schema-first governance and routing guardrails that keep traffic intentional.
The Problem
Sensitive data redaction is brittle—manual rules drift and teams lack proof it’s working.
Our Solution
Make redaction automatic with versioned policies, analyzers, and runtime validators that score coverage on every build.
The Problem
Misconfigurations lead to schema drift, broken dashboards, and surprise ingestion across log destinations.
Our Solution
Stop schema drift and turn governance into CI + runtime guardrails so dashboards, alerts, and pipelines stay predictable.
CerbiShield Dashboards
Reference Architecture
CerbiStream governs telemetry at the source, CerbiShield defines and deploys governance policy, and the Scoring API measures posture—your existing pipelines keep routing to log destinations and vendors you already trust.
Flow
- Governance policies are authored, versioned, and deployed from CerbiShield.
- Apps & services emit events into CerbiStream (source governance + validation)
- Build-time analyzers catch schema/PII violations pre-merge
- Runtime validators redact/flag (relax-mode to roll out safely)
- (Optional) governed signals enter a Scoring Queue → Scoring API → CerbiShield Dashboards for governance + risk scoring
- Your log pipeline of choice (OTel, Fluent Bit, Vector, custom) still routes payloads to vendors/sinks; Cerbi stays vendor-agnostic and never brokers traffic
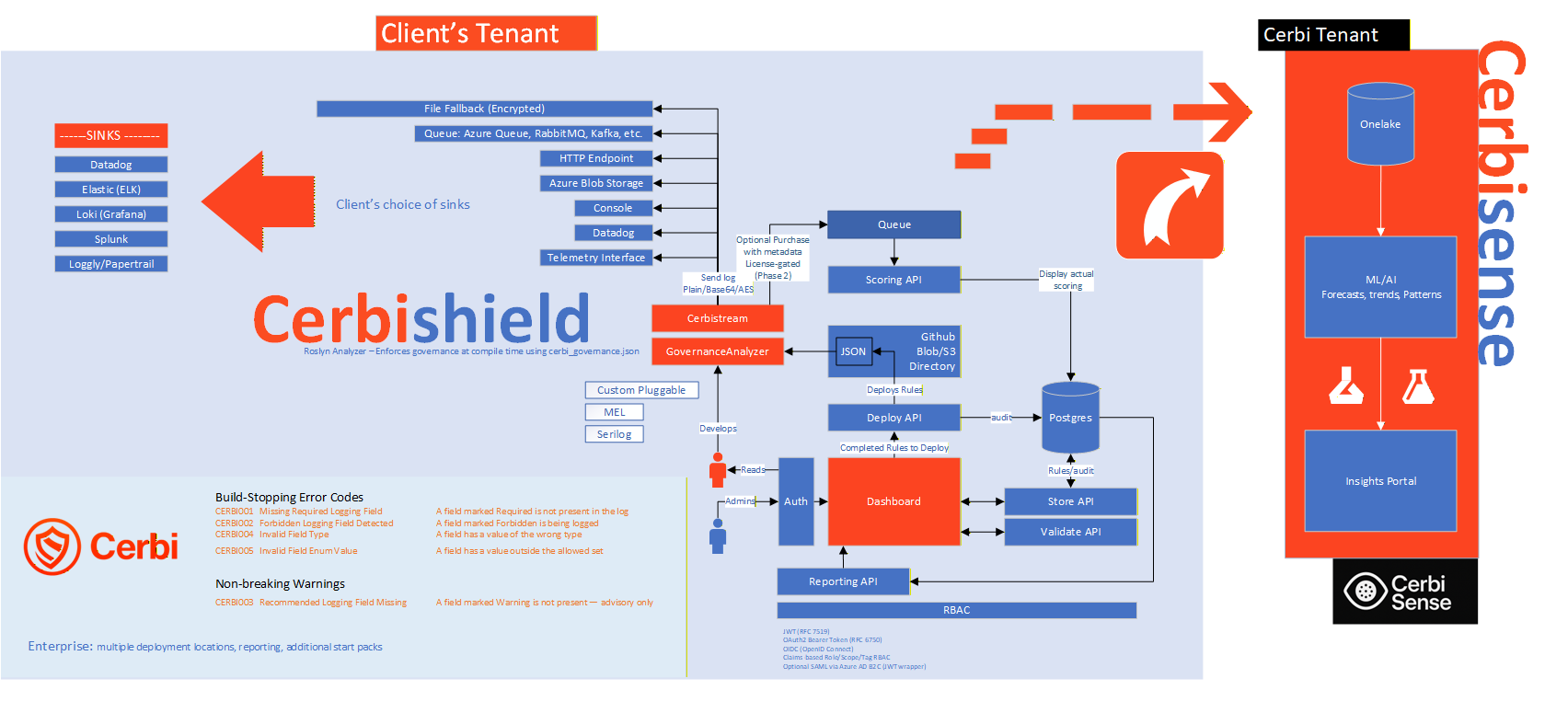
Governance you can roll out without disruption
Built for regulated tenants
- Runs inside your Azure tenant so controls stay with your team.
- Vendor-agnostic governance that sits alongside any observability stack.
- Policies-as-code keep review history and change control in familiar workflows.
Non-disruptive rollout
- No sink routing responsibility—keep forwarding data the way you do today.
- Works with existing Serilog, NLog, and MEL pipelines; Cerbi just governs the payloads.
- Customers keep their pipeline untouched while governance and scoring are layered on.
Interoperability for Devs & Execs
Keep your logger
- MEL (.NET):
builder.AddCerbiStream()adds structured output + governance. - Serilog / NLog: use analyzers at build-time and validators at runtime.
- Hybrid: keep sinks/formatters; Cerbi stabilizes field names/types and attaches correlation.
Keep your sinks
- Splunk / ELK / OpenSearch / Datadog / CloudWatch: CerbiStream governs at the source while you keep routing via OTel, Fluent Bit, Vector, or your own collectors.
- Durable dashboards: governed field names/types avoid chart breakage.
- ML-ready: consistent, PII-safe features feed analytics/LLMs.
What Cerbi does not do
Friendly reminder from the engineering team:
- We don’t replace your logging vendors or observability stacks.
- We don’t make you change sinks or collectors you already trust.
- We don’t broker or route logs—your pipelines keep doing that.
Cerbi enforces governance at the source and attaches scoring signals so the tools you already use receive cleaner, consistent data.
Install from NuGet: Cerbi Packages (live)
Install the core Cerbi packages directly from NuGet using the commands below.
CerbiStream
NuGet →Governance-enforced structured logging for .NET with optional file fallback and encryption.
CerbiStream.GovernanceAnalyzer
NuGet →Roslyn analyzer that enforces Cerbi governance rules at build time.
Cerbi.MEL.Governance
NuGet →Runtime governance adapter for Microsoft.Extensions.Logging (MEL).
Cerbi.Governance.Core
NuGet →Shared contracts and enums that keep analyzers, runtime validators, and dashboards aligned.
Cerbi.Governance.Runtime
NuGet →Runtime governance engine that evaluates Cerbi profiles and emits violation metadata.
Cerbi.Serilog.GovernanceAnalyzer
NuGet →Serilog governance plugin that enforces Cerbi profiles at runtime and ships scoring metadata into CerbiShield.
CerbiStream — Demo Overview
A deeper walk-through of the CerbiStream implementation, file fallback, governance hooks, and async logging pipeline.
Explore the Cerbi Ecosystem
From first log line to governance scores on a dashboard, each piece plays a specific role in the pipeline.
Overview
Ecosystem overview
Stage 1
Source logging
Stage 2
Build-time guardrails
Stage 3
Runtime governance & scoring
Stage 4
Shared contracts
Stage 5
Dashboards & reporting
Current Phase & What's Next
Phase 1 (Current)
- CerbiStream GA (.NET structured logger + governance tagging)
- Governance analyzers (Roslyn)
- Runtime validators (redaction, relax-mode)
- CerbiShield Beta — profiles, RBAC, audit history
- Scoring API Preview — governance scoring without owning your routing
Phase 2 (Planned)
- Scoring API — governance signal ingestion, normalization of scoring events, and rollups for dashboards
- CerbiSense — optional ML analytics on metadata
- More runtime/IDE governance experiences
Routing to external log vendors is outside Cerbi; your pipeline remains in control.
Video Library
Cerbi — Brief Overview
Quick introduction to CerbiSuite's enterprise governance platform and its core capabilities.
CerbiStream — Demo Overview
Hands-on demonstration of CerbiStream's structured logging capabilities and real-time monitoring.
CerbiSuite — Architecture & Roadmap
Walk through how CerbiStream, the analyzers, runtime validators, and CerbiShield fit together in a real deployment pipeline, and what’s coming next.
Logging PII-safe Scoring
How Cerbi keeps sensitive scoring data governed end-to-end while preserving observability fidelity.
See the Full YouTube Library
Browse every walkthrough, webinar, and launch clip directly on our channel. New uploads appear here automatically.
Why I Built CerbiSuite
A candid walkthrough for leaders and architects on where Cerbi fits: what problem it solves, what it doesn’t do, and how it plugs into the stack you already have.
Meet the person (and cats) behind Cerbi
Hi, I’m Tom Nelson — principal architect, Cerbi founder, and the one to blame for the phrase “governed telemetry.” Cerbi started as a nights-and-weekends experiment to stop our .NET logs from turning into an expensive, ungoverned mess.
Most of my work has been in regulated stacks — healthcare, insurance, payments — where “we’ll fix the logs later” usually means “we’ll suffer during the audit.” Cerbi is my answer to that: make logging predictable, compliant, and actually useful instead of noisy.
The supervising fur team is Leo and Cora. They don’t care about log volume, but they absolutely care if I miss dinner or break a dashboard on purpose to test governance.


Get in Touch
Questions, enterprise inquiries, partnerships, or funding conversations? Send a note and we'll respond quickly.